LAPS (Local Administrator Password Solution) is a free and helpful tool that Microsoft recommends for local administrator password management.
Below you will find a step-by-step walkthrough to install and configure LAPS.
What Is LAPS Used For?
One of the most detrimental misconfigurations on a Windows network is setting the same password for all local administrator accounts. It happens everywhere. Even if you’ve streamlined your endpoint rollouts with imaging software, it’s just easier to make that admin login the same across the organization. The support staff and management software can use it without needing to worry about remembering a password schema. Who else can benefit from this ease of configuration? Malicious actors, worms, viruses, ransomware just to name a few.
Once a password hash has been stolen, it can be used over and over again on any computer that has that same user/password locally. A common tool for this credential stealing is Mimikatz, a tool that can dump passwords and other authentication methods such as kerberos tickets out of memory and use those to escalate from a normal under-privileged account to an administrator account.
The primary defense against Mimikatz (and other privilege escalation) is limiting administrative privileges to only those users that need it. That’s definitely easier said than done, especially in an enterprise environment that has been around for a long time. It’s common to start at a company where you find a network that was built without design or security in mind. Many times least privilege wasn’t a consideration when a piece of software or business function just needed to work.
Luckily in 2015 Microsoft came up with an integrated solution for this. LAPS enables admins to manage the local account passwords of domain-joined computers.
LAPS protects these passwords by storing them in an access-control list (ACL) within AD (Active Directory), so only users with access rights can read or request a password reset.
System Requirements For Microsoft LAPS
Before you install LAPS, ensure that you meet the following prerequisites:
Management Tools:
- .NET Framework 4.0
- PowerShell 2.0 or higher
OS Requirements:
- Windows Vista SP2 or higher, which includes:
- Windows 7
- Windows 8
- Windows Vista
- Windows 8.1
- Windows 10
- Windows Server 2003 with current SP or higher, which includes:
- Windows Server 2003
- Windows Server 2008
- Windows Server 2012 R2
- Windows Server 2012
- Windows Server 2016
- Windows Server 2019
Active Directory Requirements:
- Windows Server 2003 SP1 or higher
Note: If you run these steps on a domain controller, ensure that nothing in the environment is using the default Domain Administrator account by checking authentication logs (event_id’s 4624, 4625, 4776). Installing LAPS on a DC will automatically change the password for the default administrator account to a random string.
For a video walkthrough, watch:
Deploy Software
Step 1: Download the LAPS msi file from Microsoft https://www.microsoft.com/en-us/download/details.aspx?id=46899
Step 2: Create a share with .msi file for domain users and COMPUTERS. This share will need to be read accessible from the users and computers that the GPO is applied to, so if you already have a share that is being used for this purpose, that would be a good candidate. If you are not deploying the package with a GPO, you can skip this step.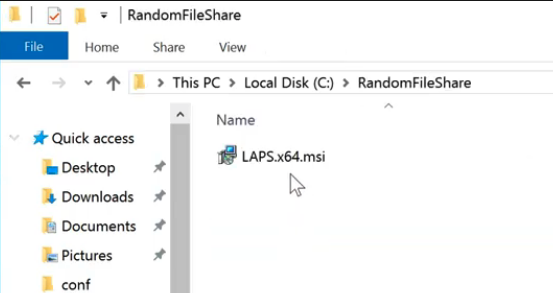
Step 3: Create a new GPO, or use an existing GPO to configure and deploy as a software package to domain-joined computers. You may also use whatever other software that you manage remote software rollout with. 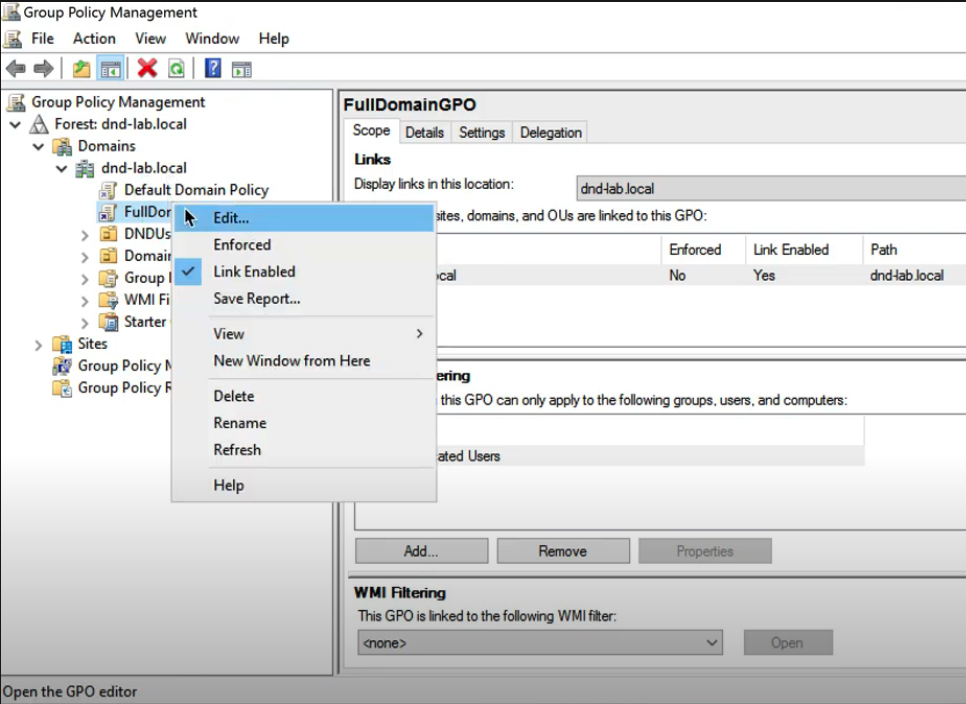
Step 4: Edit the GPO. Computer Configuration > Policies > Software Settings. Right click on Software Installation and click New > Package. = \\TEST-DC\RandomFileShare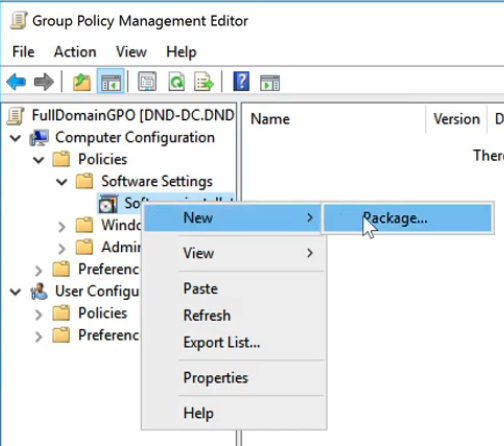
Step 5: Leave the “Deploy Software” options default, and click OK.
Extend AD Schema and Modify Permissions
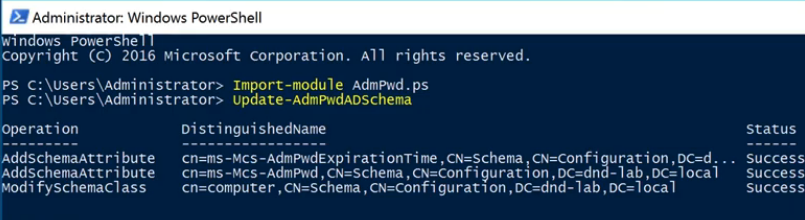
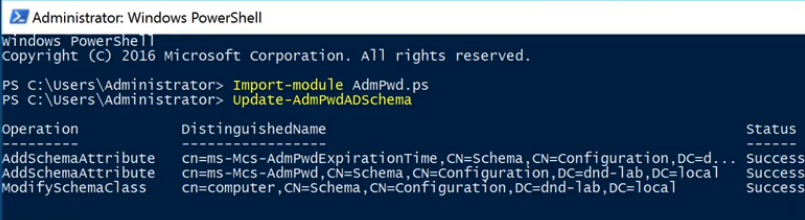
Step 1: Open PowerShell on a Domain Controller (DC)
Import-module AdmPwd.PS
Update-AdmPwdADSchema
 Step 2: The next step is to delegate endpoints to change their own passwords. More than likely you already have a set AD structure for where endpoints are located. You’ll need to repeat Steps 2-4 for each container that you will configure LAPS for. In this example, we have a new OU called “Endpoints” where all of our endpoint accounts will reside.
Step 2: The next step is to delegate endpoints to change their own passwords. More than likely you already have a set AD structure for where endpoints are located. You’ll need to repeat Steps 2-4 for each container that you will configure LAPS for. In this example, we have a new OU called “Endpoints” where all of our endpoint accounts will reside. Set-AdmPwdComputerSelfPermission -OrgUnit “Endpoints”
 Step 3: You may need to remove attributes that allow computers or users to read their own passwords. (We’ll set up who has these permissions later): Check to see who has access by typing
Step 3: You may need to remove attributes that allow computers or users to read their own passwords. (We’ll set up who has these permissions later): Check to see who has access by typing Find-AdmPwdExtendedrights -identity “Endpoints”
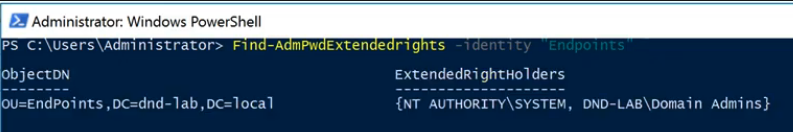 Step 4: Ideally, the groups listed should be the system account (so the computer itself can read/change for LAPS to correctly work) and any power user group that should have local administrative rights to the endpoint.
Step 4: Ideally, the groups listed should be the system account (so the computer itself can read/change for LAPS to correctly work) and any power user group that should have local administrative rights to the endpoint.
Remember, you can plan these out so different user groups have access to different endpoint OUs in Active Directory. It’s not an “everyone gets admin” type of situation.
a. Edit these by navigating to Cmd > and typing adsiedit
b. If a domain isn’t listed, right click on ADSI Edit > Connect to.. > and select your domain
c. Right click OU > Properties > Security > Advanced
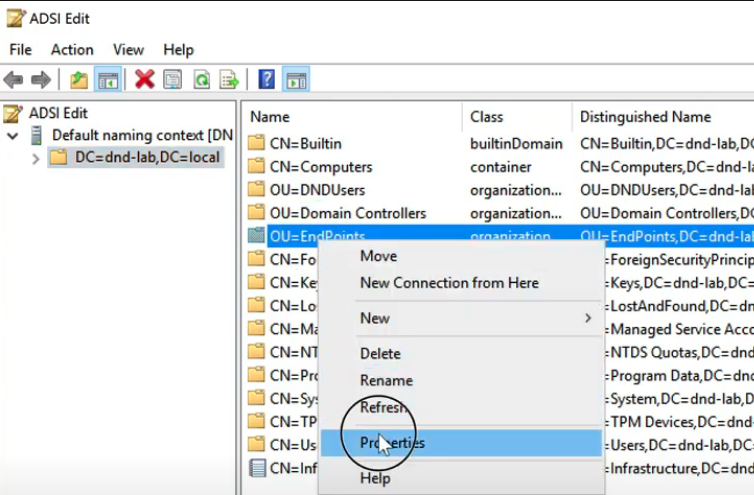 d. Locate the user that you want to edit
d. Locate the user that you want to edit
e. Navigate to the permissions below and set to the desired settings:
-
-
- Read ms-Mcs-AdmPwd
- Write ms-Mcs-AdmPwd
-
Step 5: Add the ability of a user or group to retrieve a computer’s password. In this example, we’ll allow the PowerGroup to retrieve the passwords from any device in the Endpoints OU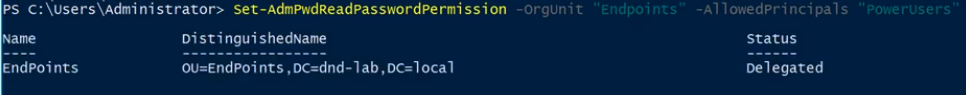 Set-AdmPwdReadPasswordPermission -OrgUnit “Endpoints” - AllowedPrincipals “PowerGroup”
Set-AdmPwdReadPasswordPermission -OrgUnit “Endpoints” - AllowedPrincipals “PowerGroup”
When you check permissions again, you see the PowerUsers is now listed. 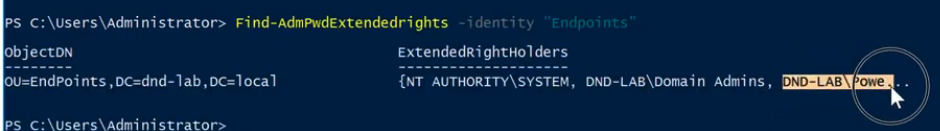
Apply Password Security
Step 1: To apply the password security and enable LAPS, you can modify this setting in the GPO you’ve already created for LAPS, or wherever makes sense in your organization’s structure.
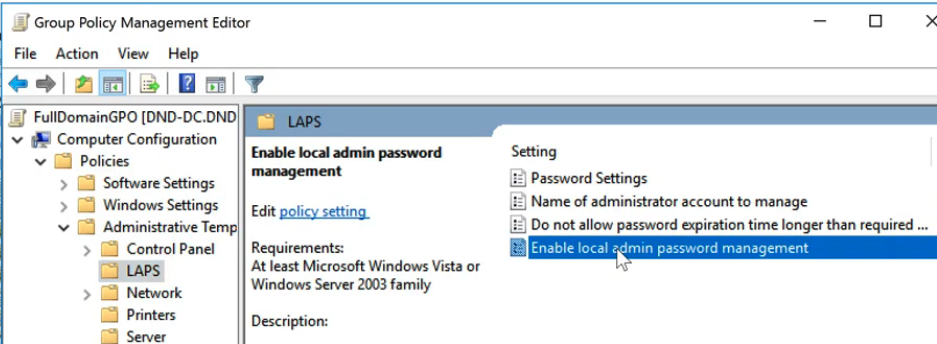
- Edit GPO > Computer Configuration > Policies>Administrative Templates > LAPS
- Enable > Enable local admin password management
 Step 2: By default this solution uses a password with maximum password complexity, 14 characters and changes the password every 30 days. You can change the values to suit your needs, however.
Step 2: By default this solution uses a password with maximum password complexity, 14 characters and changes the password every 30 days. You can change the values to suit your needs, however.
Using LAPS
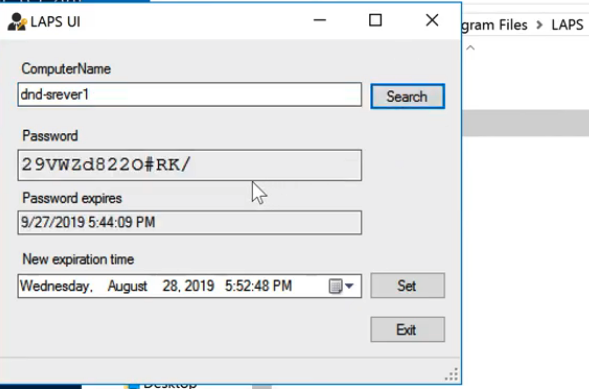
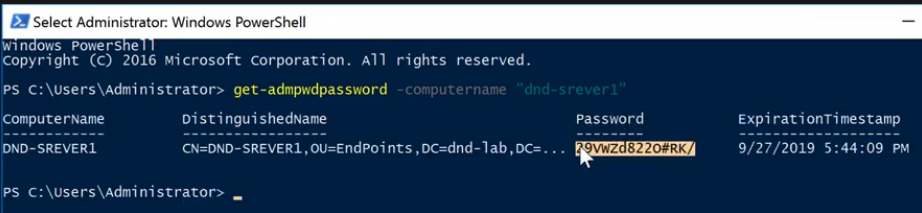
Step 1: Show password with PowerShell
-
get-admpwdpassword -computername “test-win10”- Author’s Note: disregard the misspelling of “Server” in the screenshots, it probably bothers me more than it does anyone
 Step 2: Show password with GUI
Step 2: Show password with GUI
-
- C:\Program Files\LAPS\AdmPwd.ui.exe
What To Know When Using LAPS
- It is stored in clear text in AD — but honestly, if someone is already on your domain controller you’re hosed anyways.
- Passwords are protected by ACL
- Passwords are not replicated to RODC (read-only domain controller) and not revealed in audit logs
- Passwords are protected in transit by LAPS tools
- There is an SCCM (System Center Configuration Manager) add-on to manage LAPS