Can’t Access ADMIN$ Share Using A Local User Account
Purpose:
When supplying the appropriate user credentials that have local administrator access, you attempt to access a Windows Vista, Windows 7, Windows 8x, Windows 10, Server 2008 R2, or Server 2012/2012 R2 computer and receive either the error, “Access Denied – Failed to connect to ADMIN$ share” or, “Access to the path ‘\\TARGET\\ADMIN$’ is denied.”
Resolution:
The resolution section assumes the following:
- Firewall Exceptions are set up correctly: http://support.adminarsenal.com/hc/en-us/articles/220533627.
- File and Printer Sharing is enabled.
- GPO/SRP or Antivirus is not blocking access to the ADMIN$.
- Using \\X.X.X.X\ADMIN$, where X.X.X.X is the IP address of the target machine throwing the error, does not work.
- Appropriate credentials of local administrative user have been set (and tested).
If the target computer is not a member of a Windows 2003 or later Active Directory domain, the most likely cause is that the target computer has Remote UAC enabled. Remote UAC prevents local administrative accounts from accessing ADMIN$ by preventing local admin accounts from running in an elevated mode from a network connection. To access ADMIN$ using a local account, Remote UAC will need to be disabled.
To disable Remote UAC, an entry will need to be made in the registry of the affected target computer:
Navigate to,
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
Create a DWORD value called LocalAccountTokenFilterPolicy and assign it a value of 1.
A reboot is recommended but not required, however, restarting the Server service is necessary.
 NOTES:
NOTES:
* By default, when local credentials are used to access a Windows Vista (or later OS) system that is a member of a Windows Domain, this problem does not exist. Your Windows domain may still disable Remote UAC.
* Remote administrative access is denied to local accounts when a Windows Vista (or later OS) is NOT a member of a Windows 2003 or later domain.
Additional Troubleshooting:
Remote Repair Tool:
You can also use the Remote Repair tool to troubleshoot ADMIN$ (and other) issues. To use to the tool, select the troublesome machine, click Help on the main console menu and select Open Remote Repair (or press Ctrl+~).
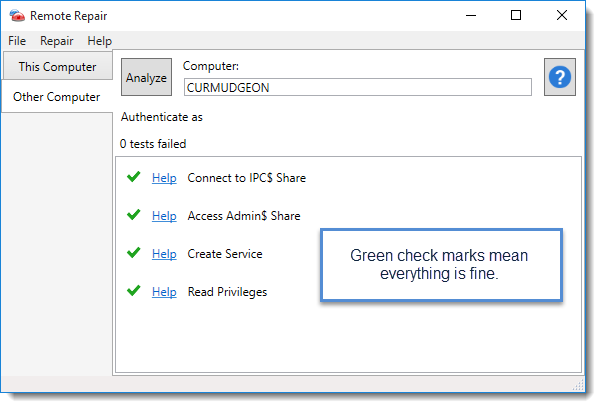
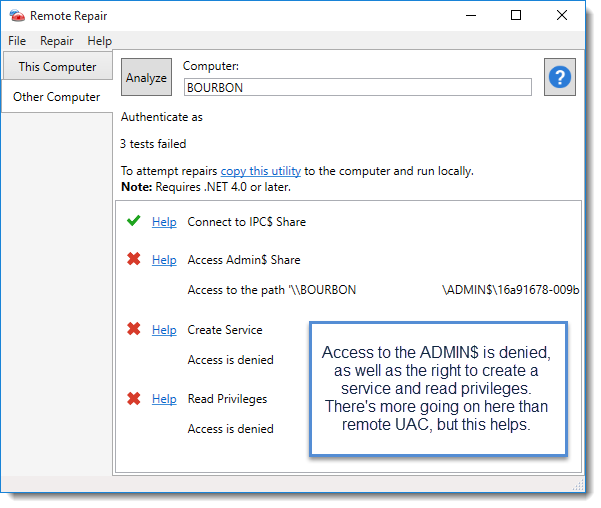
GPO and Scripts:
Check to make sure a GPO or a logon/logoff script is not specifically denying access to the ADMIN$.
Administrative Shares are Missing:
In rare cases, the administrative shares are missing on the target machine(s). You can check to see if this is the case by running the following from a command prompt and reading the results,
net share

If those shares are missing, you will need to recreate them. To do so, please see this article:
https://support.microsoft.com/en-us/kb/245117
Multiple Administrators:
In particular cases where more than one administrator is listed in PDQ’s credentials, both administrators must have explicit administrative rights on the target machine as well as the PDQ console.
Malware or Virus:
In certain rare cases, a virus or malware could also cause interesting administrative share issues.