Windows Firewall Ports And Exceptions
Purpose:
PDQ Deploy and PDQ Inventory require both console and target computers have certain firewall ports open.
In addition, use of the Central Server feature will require an additional open port on the PDQ console running in Server Mode.
Finally, using PowerShell scripts and commands will require WinRM to be enabled and the requisite Windows Firewall rules be created.
Resolution:
Firewall ports and exclusions are covered in the following:
Ports and Group Policy
Central Server
WinRM
External Exceptions
Ports and Group Policy:
The following open ports are required on the Windows Firewall (or any other firewall) for proper functionality of both PDQ Deploy and PDQ Inventory. If you can manage remote computers using standard Windows administration tools you should be set since we use the same SMB protocol:
- UDP 137
- UDP 138
- UDP 445
- TCP 139
- TCP 445
- TCP 6336 (for PDQ Deploy Central Server)
- TCP 7337 (for PDQ Inventory Central Server)
NOTE:
In light of recent ransomware attacks, it is important to note PDQ Deploy utilizes the version of SMB available in your network. In most cases, this will be the latest version, SMBv3, and will exclude SMBv1, which is the vulnerable version of SMB. SMBv1, is used by Windows XP and Windows Server 2003x, both of which are no longer supported by PDQ Deploy.
In Group Policy (recommended), the settings to open the ports above and ICMP are located in Computer Configuration > Policies > Administrative Templates > Network > Network Connections > Windows Firewall > Domain Profile
- Windows Firewall: Allow inbound file and printer sharing exception
This setting opens UDP ports 137 and 138, and TCP ports 139 and 445. This is required for the IPC$ and ADMIN$ shares to be available. Administrative access to these shares is required. (If using a local account to deploy/scan target computers, please see this article for additional configuration settings).

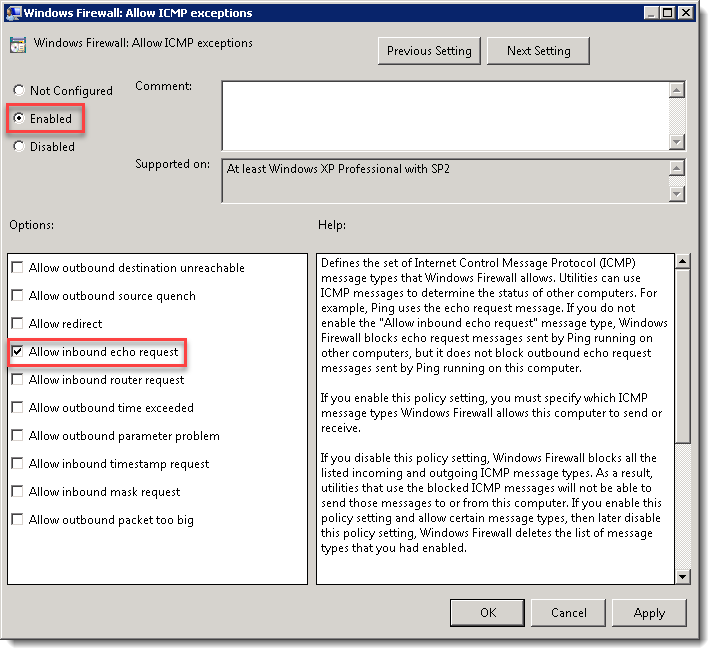
- Windows Firewall: Allow ICMP exceptions
This rule allows a target computer to respond to ping requests. Ping is used by PDQ Deploy and PDQ Inventory to determine the Online status of a computer.
- Allow inbound remote administration exception
This rule allows for remote administration. While not technically necessary since TCP port 445 is opened by Windows Firewall: Allow inbound file and printer sharing exception, this option allows for remote administration tools available in PDQ Inventory and other scripts to run effectively (see the section on WinRM for more information).

In the end, you should have something that looks like this (some additional objects have also been enabled):

NOTES:
- If you are enabling these rules on computers that are not members of an Active Directory (AD) domain then use: Computer Configuration > Policies > Administrative Templates > Network > Network Connections > Windows Firewall > Standard Profile
- If the target machine is not a member of an AD domain, you may need to disable Remote UAC restrictions. Click here for instructions.
- PDQ products ping the Fully Qualified Domain Name (FQDN) of a target or console machine to determine if it is online.
Central Server:
Central Server can automatically create a Windows Firewall rule on the PDQ console running in Server Mode. The following is from the initial setup and is also available post-install via Options > Central Server, Change Settings. This is the window in PDQ Deploy (Inventory is nearly identical).

This is equivalent to the following command (PDQ Deploy):
netsh advfirewall firewall add rule name="PDQ Deploy" dir=in action=allow program="C:\Program Files[ (x86)]\Admin Arsenal\PDQ Deploy\PDQDeployService.exe" enable=yes localport=6336 remoteport=6336 protocol=tcp profile=[domain|private]
WinRM:
In addition to the above, the use of remote Powershell requires that WinRM be enabled on all machines and that Windows Firewall be configured to allow inbound Windows Remote Management. In Group Policy (recommended) the settings are located in Computer Configuration > Policies > Administrative Templates > Windows Components > Windows Remote Management >
- WinRM Service, Allow remote server management through WinRM

- In Computer Configuration > Preferences > Services, right-click in the Services pane, select New >Service. In the General tab of the New Service Properties window, select the options as follows:Startup: Automatic
Service Name: WinRm (you can select using the […] picker or input the name manually)
Service Action: Start Service

- Configure a Windows Firewall Rule. In Group Policy go to Computer Configuration > Policies >Windows Settings > Security Settings > Windows Firewall with Advanced Security > Windows Firewall with Advanced Security. Right-click in the right-hand pane, select New Rule…. Go through the Merry Wizard:



External Exceptions:
PDQ Deploy and PDQ Inventory access the internet to perform regular tasks such as update the Package Library, Collection Library, Tools Library, and System Variables (used in collections). In addition to these regular connections, PDQ products periodically check for program updates, package updates, license expiration information, and for notifications from PDQ.com (For example, webcast notices, beta notices, etc.).
In order for these connections to function properly, PDQ products will require access to the following external sites:
https://aafiles.blob.core.windows.net
https://secure.adminarsenal.com/
https://secure.pdq.com/
You can test these connections by using Google Chrome or IE/Edge (friendly error messages turned off):
- Go to https://aafiles.blob.core.windows.net -you should get an XML error page.
- Go to https://secure.adminarsenal.com/Subscription/PackageLibrary -you should get a large XML document there outlining the Package Library.
- Go to https://secure.pdq.com/Subscription/PackageLibrary -you should get the same large XML document there outlining the Package Library from the previous test.
Go to https://secure.pdq.com/ or https://secure.adminarsenal.com/ -you should see a website was successfully created page.